Threat hunting represents a fundamental shift in cybersecurity strategy. Unlike traditional security approaches that rely on automated alerts and known signatures, threat hunting involves the proactive search for indicators of compromise (IOCs) and suspicious activities that may have evaded your existing security controls. It implies actively tracking signs of compromise that automated systems might miss to detect threats before they cause significant damage.
Speed of Detection: The True Measure of Effective Threat Hunting
While many organizations focus primarily on the volume of threats discovered, the real effectiveness of threat hunting lies in the speed of detection and response. The cybersecurity industry has long emphasized the importance of reducing mean time to detection (MTTD) and mean time to response (MTTR), and threat hunting plays a crucial role for these metrics.
Fast detection capabilities provide several critical advantages:
- Reduced attack progression which significantly decreases the potential impact of an incident.
- Minimized data exposure means less time for data exfiltration and a smaller blast radius for potential breaches.
- Cost reduction: faster detection and response cut incident response costs, regulatory fines, and business disruption.
- Competitive protection of intellectual property and trade secrets.
Accelerating Detection with Advanced Threat Intelligence
ANY.RUN’s Threat Intelligence Lookup is a powerful solution that significantly accelerates the threat hunting process. By providing access to a comprehensive database of the latest business-targeted attacks, it helps to dramatically reduce the time required to identify and contextualize potential threats.
| Use Threat Intelligence Lookup to speed up threat hunting and enhance proactive security. Start with 50 trial search requests. |
SOC analysts can query their log data and alert backlogs against the TI Lookup database, instantly discovering relevant context even for the smallest artifacts or indicators. This transforms what might otherwise be time-consuming manual research into rapid, actionable intelligence.
Example 1: IP Address Investigation
Consider a scenario where your network monitoring tools have flagged unusual outbound traffic to an unfamiliar IP address. In traditional threat hunting workflows, investigating this indicator might involve multiple manual steps: checking reputation databases, searching for historical references, and attempting to correlate the IP with known campaigns.
Using ANY.RUN’s Threat Intelligence Lookup, this investigation becomes significantly more efficient. Search for the suspicious IP address using special TI Lookup parameter. Within seconds, you receive comprehensive intelligence about the indicator.
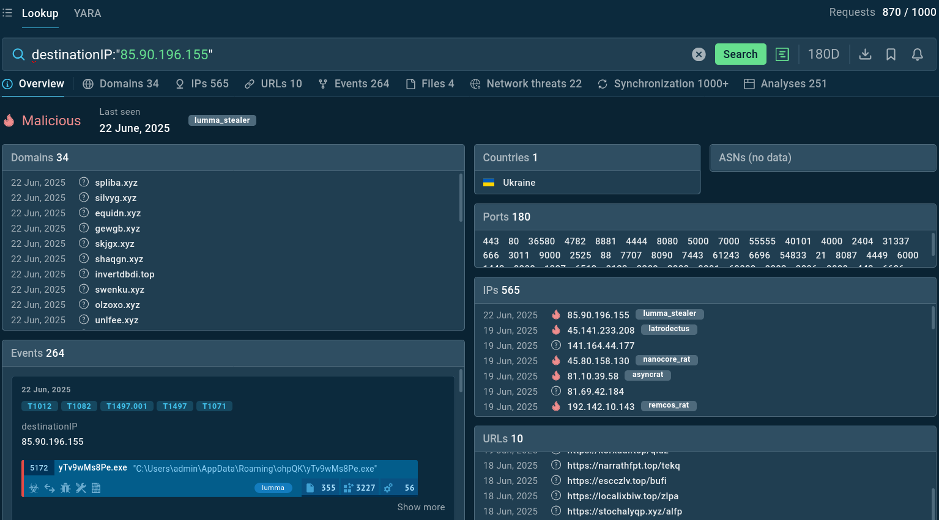
Results of searching an IP address in Threat Intelligence Lookup
The lookup reveals that the IP address has been flagged as malicious, associated with a specific malware family (Lumma stealer), and linked to recent attack campaigns.
The service provides related indicators of compromise (IOCs) that are commonly associated with this IP address. These might include additional IP addresses, domain names, file hashes, and mutexes that you can immediately search for in your environment.
TI lookup connects you to actual malware analysis sessions in ANY.RUN’s Interactive Sandbox. You can review detailed behavioral analysis of samples that communicated with this IP address, understanding exactly what the malware does, how it operates, and what other indicators you should be hunting for.
Example 2: Proactive Threat Intelligence Collection
Effective threat hunting involves proactive intelligence collection focused on threats relevant to your specific organization and industry. ANY.RUN’s Ti Lookup enables this proactive approach through targeted threat research and indicator collection.
For example, if your organization operates in the banking sector, you might be particularly concerned about information stealers like Lumma Stealer, which specifically targets financial credentials and sensitive personal information.
With the aid of TI Lookup, you can research recent Lumma campaigns and collect comprehensive indicator sets. This might include command and control domains, distribution URLs, file hashes of recent samples, and network communication patterns.
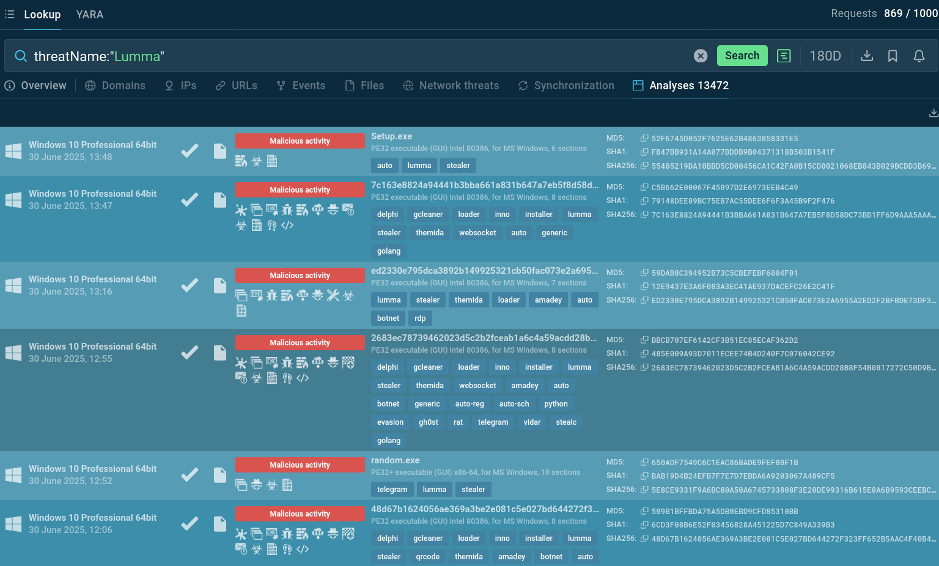
Searching by the threat name delivers links to sandbox analyses
Sandbox analyses help analysts understand how these campaigns evolve over time and provide valuable insight into attacker behavior patterns. You can track how threat actors modify their tactics, techniques, and procedures (TTPs) and adjust your hunting strategies accordingly.
Armed with this intelligence, you can create targeted rules and queries that hunt for indicators associated with these campaigns in your environment, enabling you to detect attacks much earlier in the kill chain.
Aligning Threat Hunting with Business Objectives
Effective threat hunting must be aligned with broader business objectives to ensure that security investments deliver maximum value to the organization. This involves several key considerations:
- Risk-Based Prioritization: focus on the threats that are most likely to impact your critical business processes, valuable data assets, and competitive advantages.
- Compliance and Regulatory Requirements: involve threat hunting to support compliance with relevant standards such as PCI DSS, HIPAA, or industry-specific regulations.
- Business Continuity Protection: concentrate the efforts on protecting the systems and data most essential to business operations.
- Cost-Benefit Analysis: achieve clear return on investment by preventing incidents that would otherwise result in significant business impact. This includes not only direct financial losses but also reputational damage, regulatory penalties, and competitive disadvantage.
- Integration with Incident Response: make sure that discovered threats can be rapidly contained and remediated with minimal business disruption.
Conclusion
Building an effective threat hunting workflow in your SOC requires a combination of skilled analysts, smart procedures, and powerful services like ANY.RUN’s Threat Intelligence Lookup. By proactively searching for hidden threats, correlating internal data with real-time threat intelligence, and aligning efforts with business goals, SOCs can significantly enhance their organization’s security posture. In an era where cyber threats are increasingly sophisticated, threat hunting is no longer optional; it’s a vital component of a resilient cybersecurity strategy.
Lynn Martelli is an editor at Readability. She received her MFA in Creative Writing from Antioch University and has worked as an editor for over 10 years. Lynn has edited a wide variety of books, including fiction, non-fiction, memoirs, and more. In her free time, Lynn enjoys reading, writing, and spending time with her family and friends.















